All about DNS poisoning: How does cache poisoning work?

Cybercriminals use different techniques to compromise the target systems or enterprise professionals. The increased rate of cyberattacks is putting concern among many. Attackers also target Domain Name Systems (DNS) to poison or corrupt the DNS with wrong information. It often leads to web cache poisoning.
According to recent reports, researchers discovered web cache poisoning vulnerabilities associated with many sites and received bounty rewards. This article will dig deep into the nitty-gritty of DNS poisoning, how it occurs, and the risks associated with DNS or web cache poisoning.
What is Domain Name System (DNS)?
A domain Name System is an internet phonebook or naming database that is responsible for mapping internet domain names with their respective Internet Protocol (IP) addresses. Every internet users use those domain names to go to a separate server. But, it is actually the DNS which redirects the users to the specific IP address.
Let’s suppose a user wants to visit Google. He will type this www.google.com string in the address bar of the browser. The request will go to the DNS server where the server will check whether the URL string is valid & exist in its database. Once the map matches an IP address, in this case, it will be 8.8.4.8 or 8.8.8.8 — it will request to the server. The server will respond by displaying the page to the client.
Now to understand how DNS works and DNS caching helps the overall process, let us comprehend what DNS caching is.
What is DNS caching?
DNS caching is a temporary state found while the DNS performs its lookup or mapping operation. Keeping a local copy of the DNS lookup enables the browser to load the requested page quickly. A DNS resolver delivers the user with the IP address for a particular domain name. DNS caching will temporarily save the responses to IP address queries in a cache when the resolver provides it. But DNS caching does not only occur at the web browser or OS level.
Cache keys
When the cache receives an HTTP request, it first has to determine whether there is a cached response that it can serve directly, or whether it has to forward the request for handling by the backend server. Caches identify equivalent requests by comparing a predefined subset of the request’s components, known collectively as the “cache key”. Typically, this would contain the request line and Host header. Components of the request that are not included in the cache key are said to be “unkeyed”.
If the cache key of an incoming request matches the key of a previous request, then the cache considers them to be equivalent. As a result, it will serve a copy of the cached response that was generated for the original request. This applies to all subsequent requests with the matching cache key until the cached response expires.
Crucially, the other components of the request are ignored altogether by the cache. We’ll explore the impact of this behaviour in more detail later.
What is web cache poisoning or DNS poisoning, or DNS cache poisoning?
Web cache poisoning or DNS poisoning is an internet-driven attack where the attacker exploits a web server vulnerability associated with caching the server. The attacker serves false information or malicious HTTP response, dragging the user’s browsing to an incorrect or unsolicited web page. The impact of manipulated response will depend on how or where the attacker targeted the attack. Mostly, attackers target shared web cache, such as in proxy servers, to impact mass users.
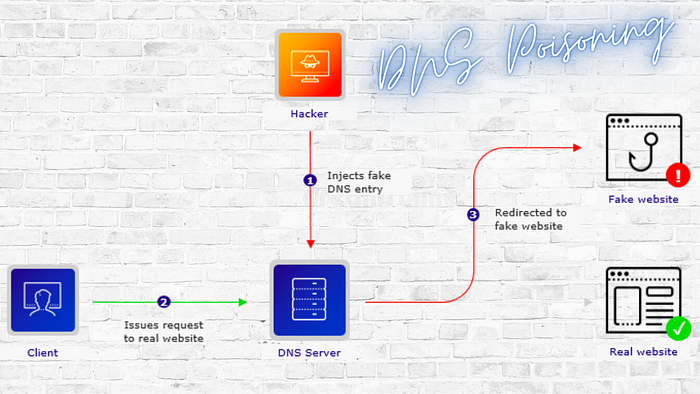
Such an attack usually redirects users to illegitimate sites, malicious sites from where malware or browser hijacking program gets downloaded automatically into user systems from rogue servers/locations. Such web cache poisoning attacks often damage the company’s or brand’s reputation. It becomes challenging to verify the data stored in their caches that got corrupted. It means that the incorrect information resides in that cache until the time to live (TTL) value expires or security professionals resolve this issue manually.
How web cache poisoning occurs/work?
Once the attacker gains access to the DNS server; the attacker will put the fraudulent IP address or malicious server information in there. It will compel the DNS resolver to redirect to the malicious site instead of the actual one. Attackers can successfully poison the web cache if the DNS is meant for smaller internet users & does not have proper security measures in place. In this attack technique, the attacker tries to breach the integrity of the DNS, redirecting the user to illegitimate sites.
Because of these intrinsic and longstanding flaws, attackers can hijack the DNS cache and change its original data with hostile ones. Attackers often perform web cache poisoning to increase another website’s traffic, download malware in the victim’s system, generate vicious responses, damage the regular business workflow, or harm the brand’s reputation. Other than malware infection, web cache poisoning, data integrity, hampering security updates, and misleading users are popular motives for cache poisoning.
What can happen if your DNS gets spoofed or poisoned?
⦾ Data theft -> The attacker can compromise every type of data like your password, your credit card details, and your address.
⦾ Viruses/Malware -> The attacker can download malicious software or viruses into the computer which will harm the computer badly.
⦾ Stopped security updates -> If the internet security provider is spoofed it will not download the latest security updates and your device will be exposed to malware and trojans.
How to protect against DNS poisoning?
Here are some effective ways enterprises can prevent DNS poisoning.
i. Enterprises should use DNS Security Extensions (DNSSEC) protocol. It signs security policy at various DNS lookup levels, preventing poisoning of the DNS cache.
ii. Various DNS spoof detection tools exist in the market. It confirms whether the DNS responses are legitimate.
iii. Use a caching plugin that is made available by WordPress, so that if someone gets an error accessing your website, they will be able to see an older version of the page that you’ve made available through a cached version.
iv. Implementing end-to-end encryption is another technique to keep adversaries at bay from putting illegitimate information into the cache — hence, preventing web cache poisoning.
v. When you change the content of your pages, make sure to remove any cached versions.
vi. Enterprises can follow certain best practices like leveraging Virtual private network (VPN) applications and flushing our DNS cache to resolve poisoning issues.
vii. Enterprises can also hire penetration testers, vulnerability detection teams, or security experts like Packetlabs to identify flaws in systems like JavaScript injection, cross-site scripting (XSS), and open redirection that may lead to web cache poisoning.
viii. Always make sure that your site is well optimized so that caching results in pages loading faster, and not error messages when people are refreshing or trying to access your page. Also, make sure that you have images on your site which are well-optimized for performance.
ix. Never use the same image over and over again in your blog posts, as this will make it easier for web cache poisoning to work on your site.
Tools Used to check DNS spoofing —
➡ Dnsspoof: This tool navigates all the DNS to a fake local computer host file.
➡ Ettercap: It is one of the best tools for man-in-the-middle attacks(MITM) and it provides DNS spoof, arp spoof, and a lot more options for MITM
➡ Arpspoof: This tool commands the IP address.
Conclusion –
We can conclude that some measures & best practices can prevent businesses from web cache poisoning attacks. However, enterprise security professionals should also consider regular browser patching, scanning systems using anti-malware, etc., for more precautions. If you want to dodge such a daunting vulnerability, try contacting Packetlabs experts.
If you want such technical content or article for your B2B or B2C business, contact me here. Having 7+ years of experience in writing, I write outstanding and versatile technical and non-technical content featuring infographics, animations, and SEO strategies that can bring potential leads & audiences to your website. You can ultimately enjoy more visibility and traffic on your website. The price/project or price per word is negotiable.
